How to use bitcoin anonymously?
As you probably already know, bitcoin is not anonymous (this property was never part of its original design). Bitcoin transactions are chained together in a permanent public record. Analysis of the blockchain may reveal a lot information about your transactions [1] (e.g., recipients of your payments, addresses in your wallet or the balance of your wallet). The following sections contains everything you need to know in order to prevent such kind of blockchain analysis.
There are currently three main methods how you can make your transactions more private. The first method is called CoinJoin [2] and is based on "joining" your transactions with transactions of other users. Most advanced project based on this method is JoinMarket [3]. This method is very secure, but unfortunately not fully implemented yet. However, the development process continues and the user base is slowly growing. The second method is called Confidential Transactions [4]. In simple terms, this method encrypts amounts in your transactions and helps obfuscate chain of the transactions. This method is not yet part of bitcoin implementation, but may be implemented in the future.
Figure 1: Basic workflow of a Bitcoin Mixing Service
The oldest and most often used method is bitcoin mixing (see Figure 1) which works on similar basis as mix network [5]. The bitcoin mixer receives bitcoins to input addresses and sends out different amounts from different input address. This method requires trusting the mixer, but is sufficiently secure when used properly. Manny of our users mix their bitcons for the first time. Because mixing your bitcoins properly requires to follow some simple rules, we decided to write a manual that will make this operation much easier.
Buying bitcoins
The first step is of course to get some bitcoins. Unfortunately, there is no easy way to buy bitcoins fully anonymously (we will solve that problem later). Most of the bitcoin exchanges have Know Your Customer (KYC) policy. That means you have to provide your ID, driver's license or passport before buying some bitcoins. Even when the identity verification is not required your bitcoins will be still linked to your bank account or your face (when buying in person). Therefore, feel free to chose the service which requires the lowest possible amount of information.
We recommend using LocalBitcoins.com, since you can buy bitcoins quickly via this service without identity verification in many countries. However, we don't recommend using Tor Browser with this service, because some bitcoin sellers won't sell the bitcoins to you if you are connected via Tor. LocalBitcoins.com is good service, especially if you prefer wire transfer or buying bitcoins in person. It is also possible to buy bitcoins at your local bitcoin ATM or with debit card via circle.com. Unfortunately, not all debit/credit cards are accepted.
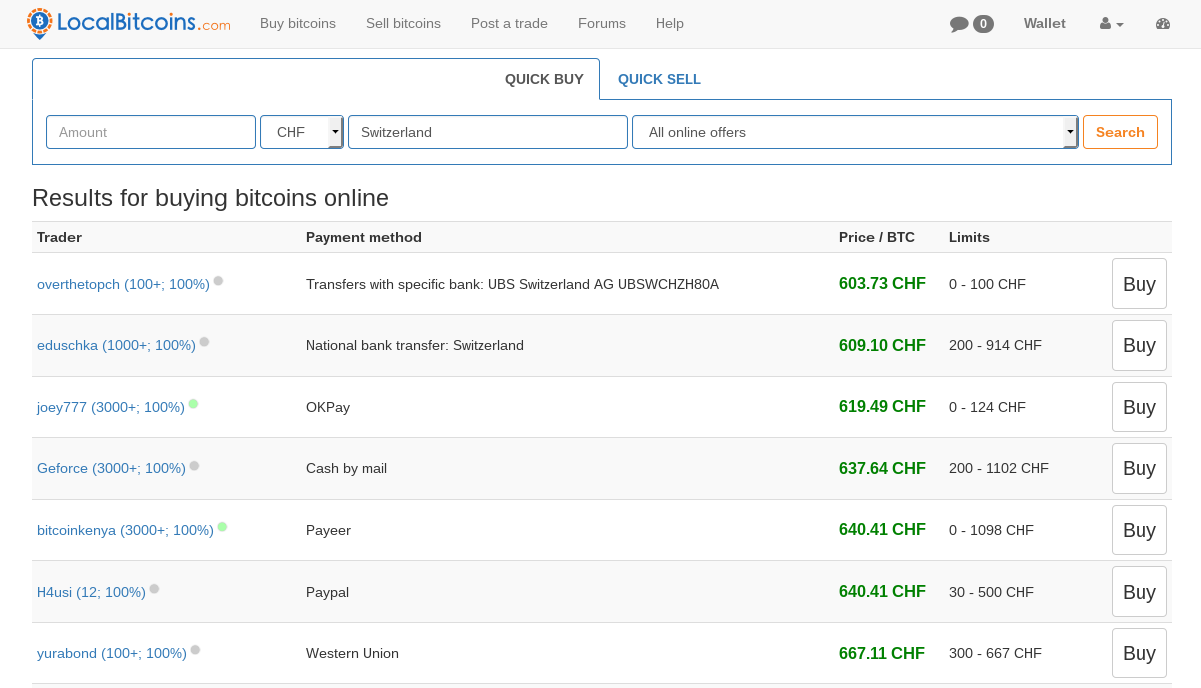
Figure 2: Buying bitcoins via LocalBitcoins.com
Anonymous wallet
Ok, let's assume we already have some fresh bitcoins from the bitcoin exchange. The second step is to create anonymous wallet. We will keep the mixed bitcoins in this wallet and also send anonymous payments from it. The most secure wallet is full bitcoin client (e.g., Bitcoin Core). However, this kind of wallet requires over 80 GB of hard drive space, generates a lot of network traffic and may be complicated for new bitcoin users.
If you cannot afford such luxury there is also Electrum wallet. The Electrum wallet is an SPV client [6]. It is also very secure and requires very low amount of space on your hard drive. We will use it as an example in our manual. Download the Electrum wallet from its official website and install it. Download also standalone version of Tor (without Tor Browser) and install it. You will need it to connect to Electrum servers via Tor anonymity network. The Tor will listen on TCP port 9050 after the installation. There is no need to change the default Tor settings, but don't forget to change the configuration of Electrum: Electrum: Tools → Network (for the proper configuration of network see Figure 3).
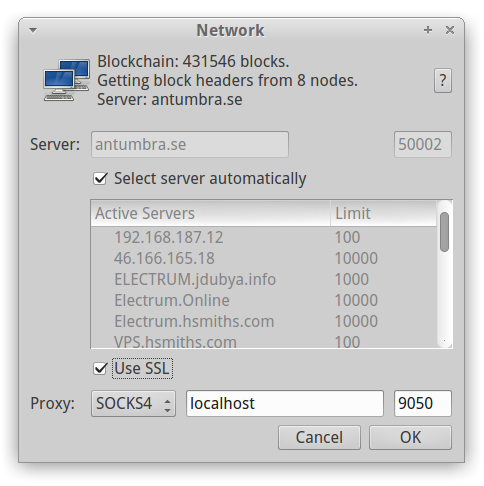
Figure 3: Tor configuration in Electrum
If you run the Electrum for the first time it will challenge you to create a new wallet. (see Figure 4). Do not create the new wallet before the network is properly configured to use Tor! Give some name to the wallet and continue.
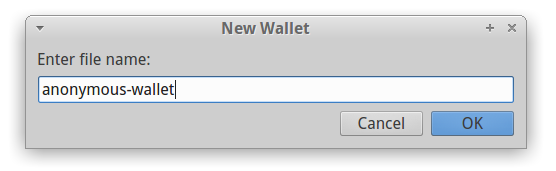
Figure 4: Create new anonymous Electrum wallet
Select the standard kind of the wallet on the next dialog and continue (see Figure 5).
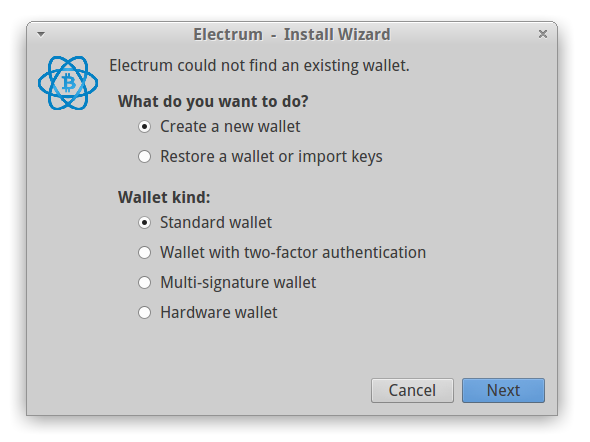
Figure 5: Select type of Electrum wallet
Electrum will challenge you to save the wallet generation seed in the next step (see Figure 6). You will need the seed if something bad happens to the wallet, so keep it in safe location and private (the seed on the picture is from empty wallet, so we can make it public, but you shouldn't).
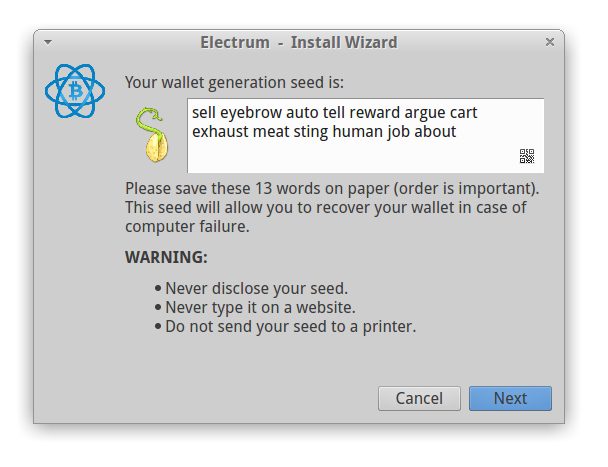
Figure 6: Save the wallet generation seed
Great, you are almost done. Switch to Receive tab and create some output addresses for the mixing service. We will use them later to send some bitcoins to the wallet. Optimal number of output addresses is 2-5.
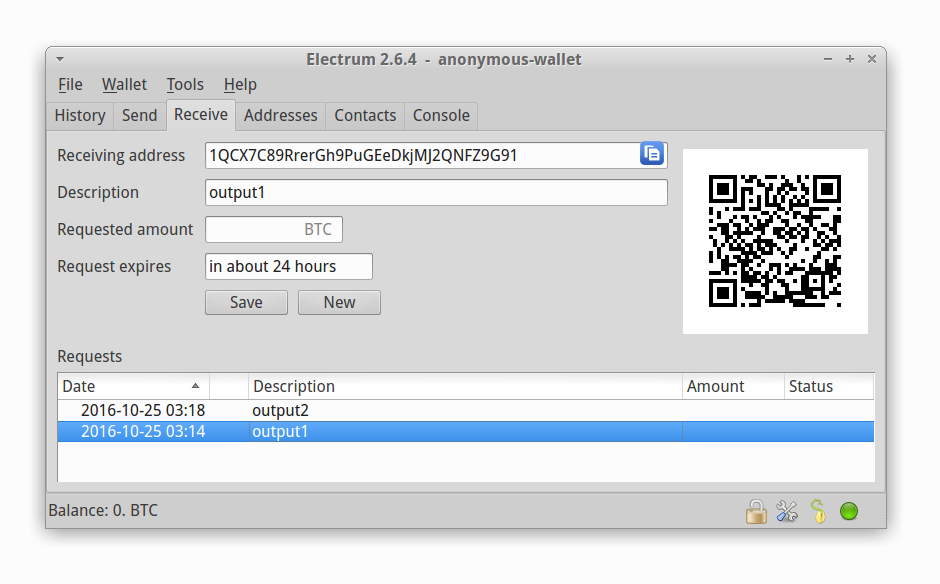
Figure 7: Create a few output addresses
Mixing bitcoins
The last part is mixing the bitcoins. We will send the bitcoins anonymously from LocalBitcoins.com to the anonymous wallet via coinmixer.app. Open our website in the Tor Browser and click on Participate link. Copy the output addresses from the previous step to the output fields. The sum of the output values makes the overall mixed value. There is also the delay value. A longer delay means that your participation will be more resistant to blockchain analysis (better anonymity, but it takes a longer time). We recommend setting different delay for each output. It is possible to set the delay to 0, but it is not recommend because it reveals in which block the outputs are.
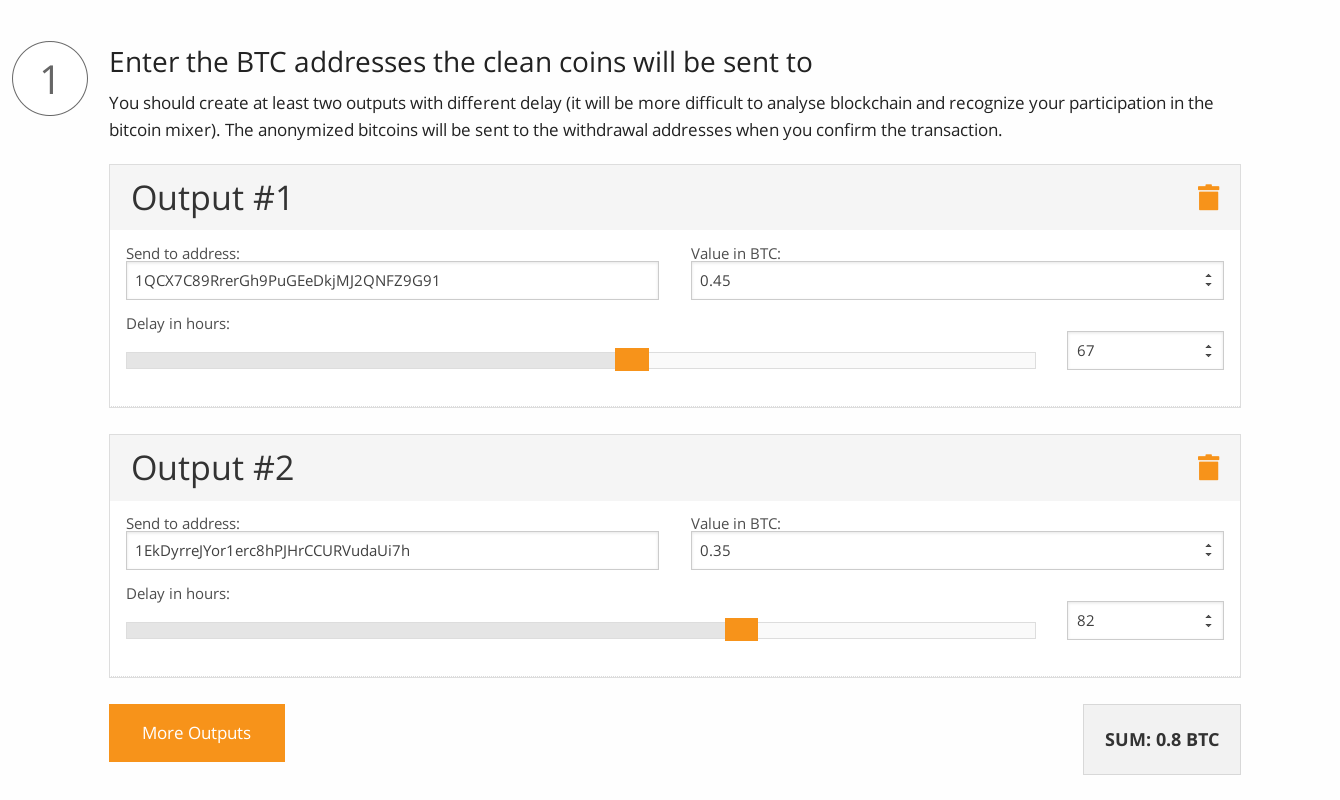
Figure 8: Create a new participation
The next step is simple. Just rewrite the captcha code and click on the continue button (see Figure 8).
Figure 9: Rewrite the captcha code
We are almost there. We just need to confirm the participation and the system will take care of the rest. You can chose from three transfer methods. We will chose "Address and Amount", since we need to send the bitcoins from LocalBitcoins.com.
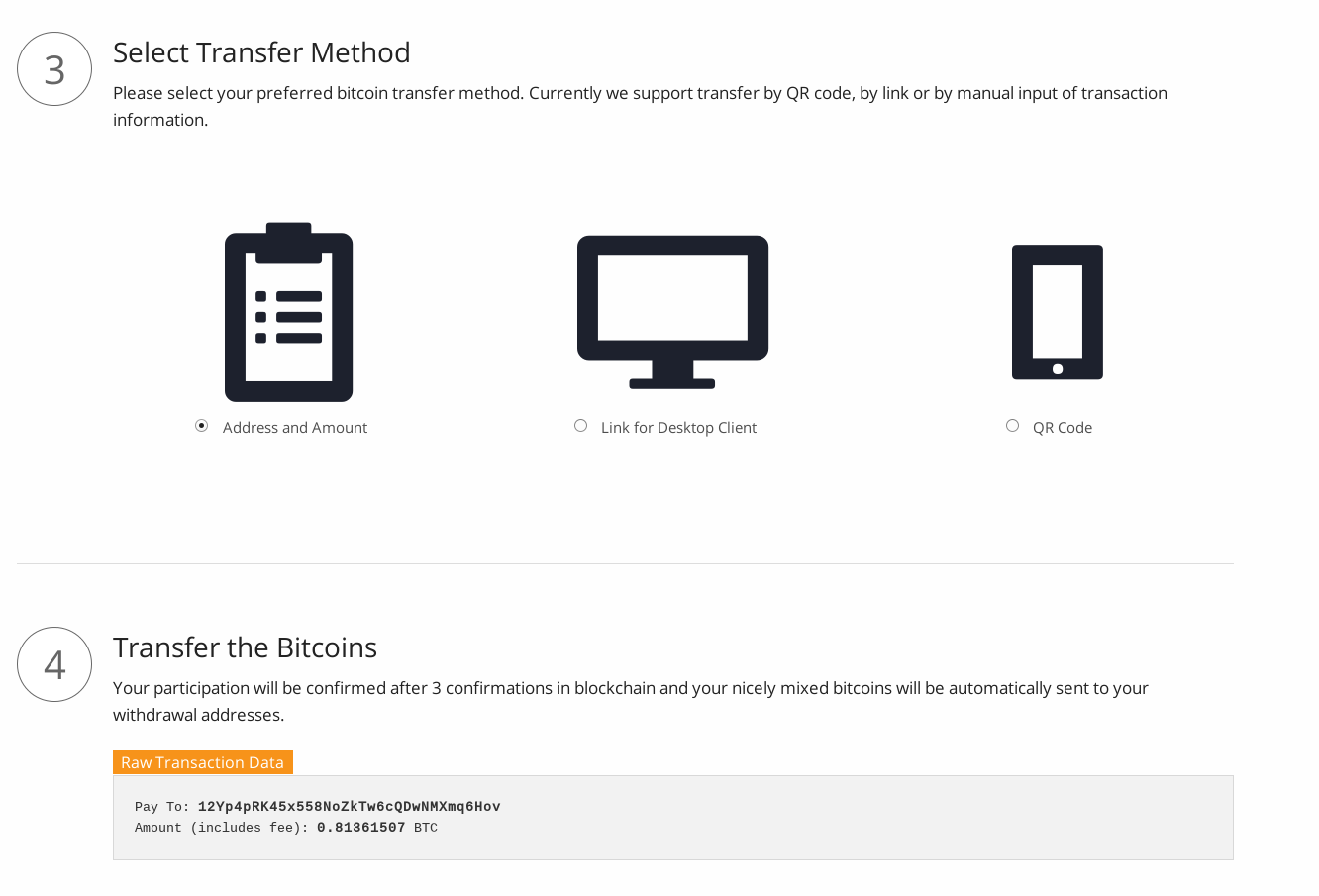
Figure 10: Transfer of bitcoins
Don't forget to save the Letter of Guarantee. It is important.
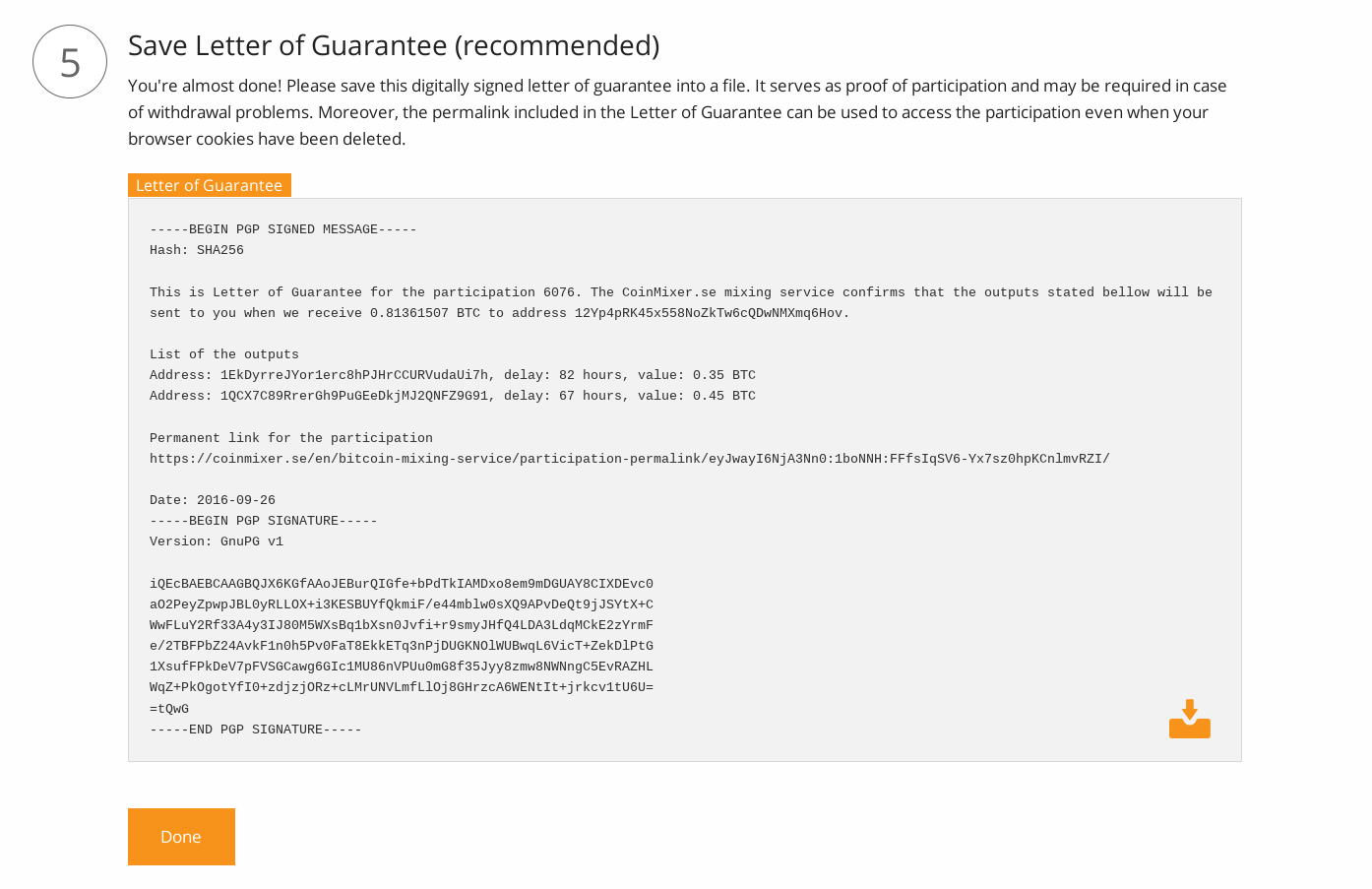
Figure 11: Letter of guarantee
We will copy the payment information exactly as it is to the LocalBitcoins.com payment form and send it.
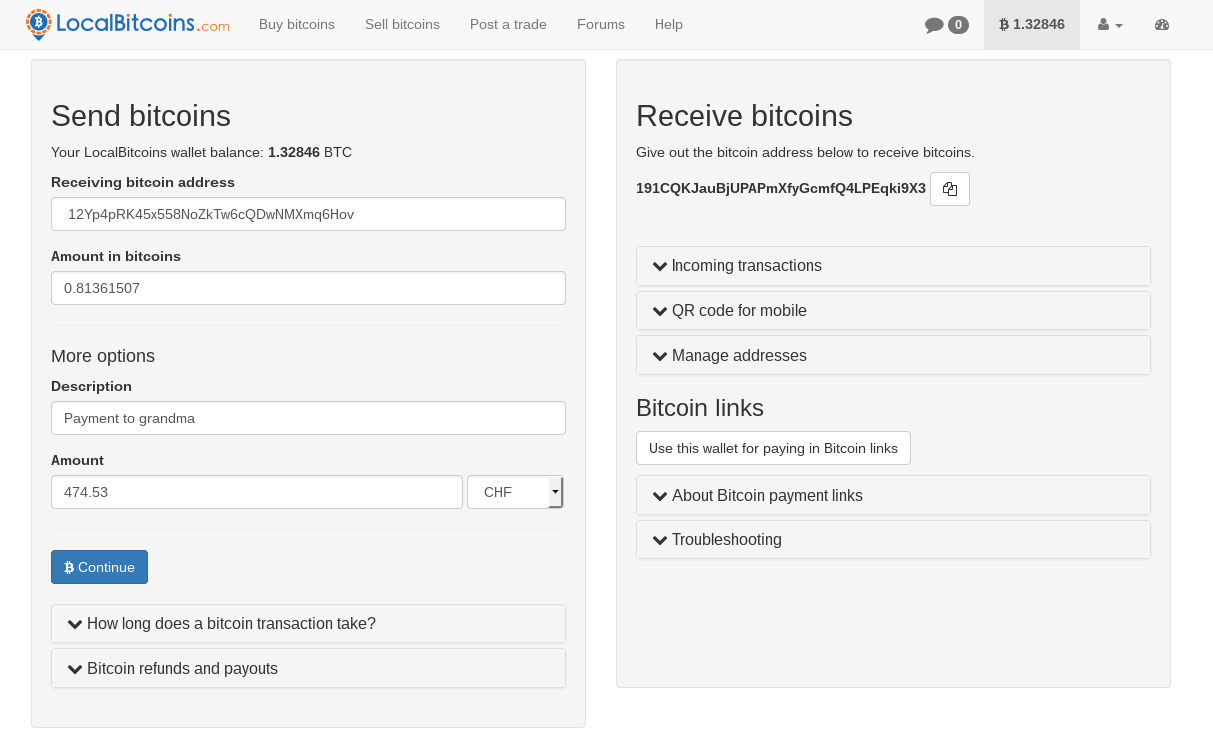
Figure 12: Sending bitcoins from LocalBitcoins.com
Your participation will be confirmed after 3 confirmations in the blockchain (see Figure 13).
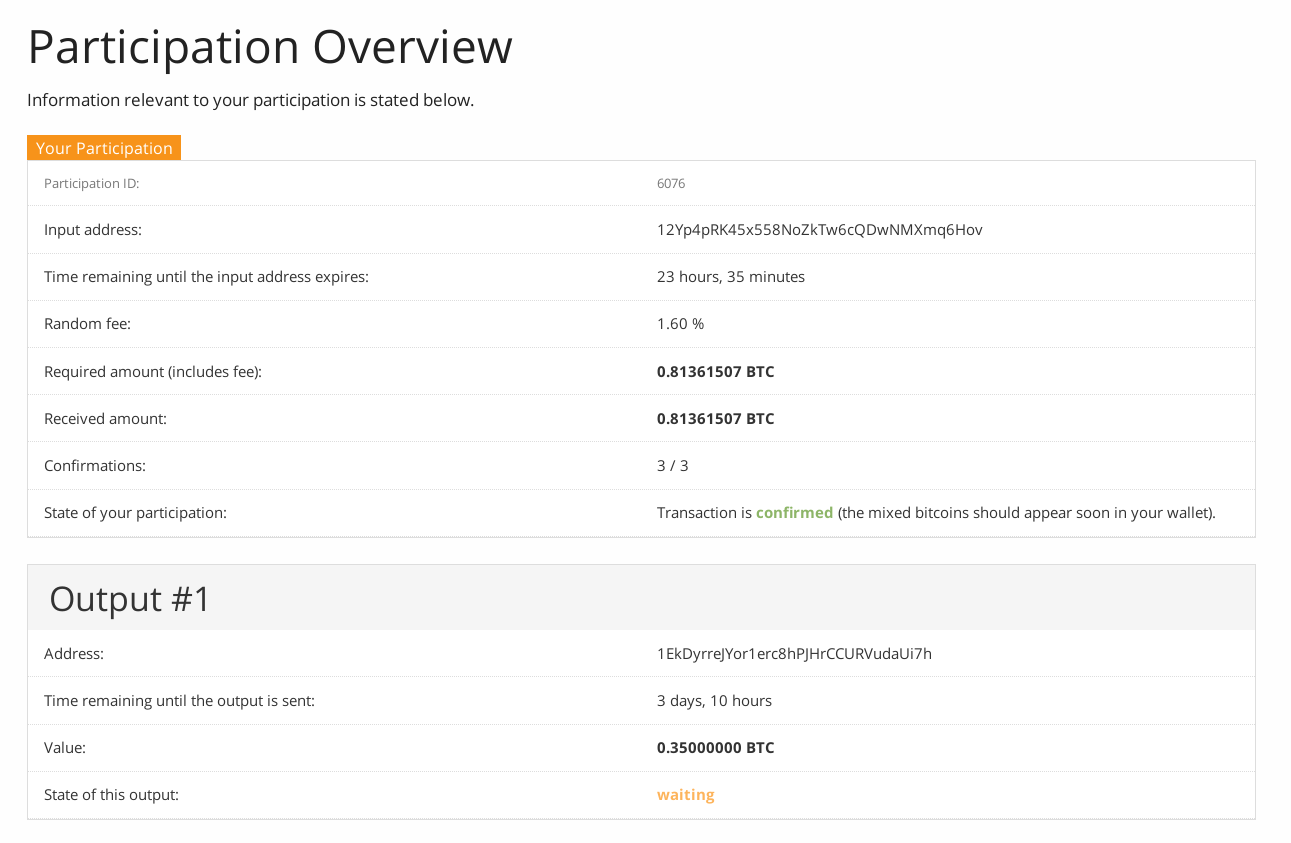
Figure 13: Participation is confirmed
And that's it. Your bitcoins will be send with delay you provided in the participation form (see Figure 14). Thank you for reading this manual.
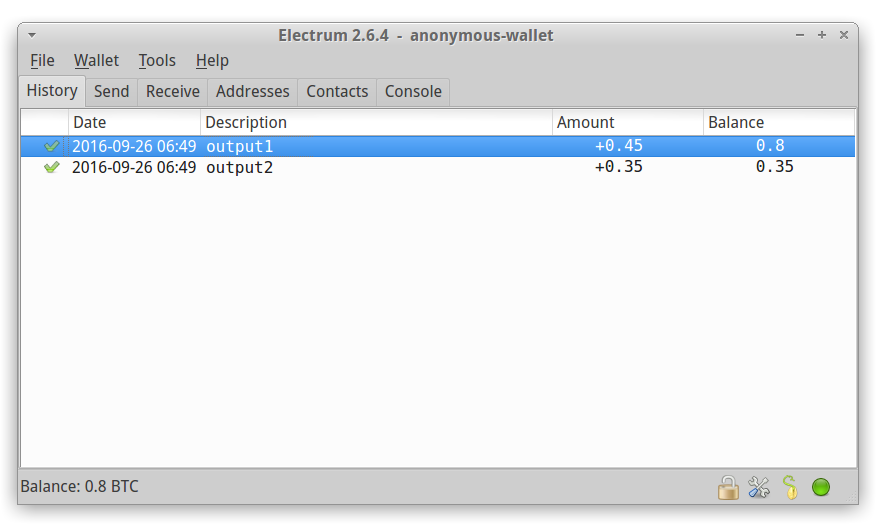
Figure 14: The bitcoins have been received
Selling bitcoins
Our users often ask us if the mixed bitcoins are "clean" bitcoins. In other words, they ask if they may sell the bitcoins directly to a third party. The bitcoins you get from us have no connection to your own identity, but they have a connection to multiple identities of other users (as every bitcoin does).
In most cases and in most jurisdictions you may sell the bitcoins directly. However, companies like Coinbase and many others are known to keep track of incoming and outgoing transactions. If you want to sell the bitcoins to a service which censors the transactions and may reject the transaction because of it's origin (e.g., the Coinbase), then we recommend cleaning the coins even further. This can be done by using any service which allows you to deposit bitcoins on a bitcoin account and withdraw them later. Therefore, it is a legit origin of the transaction.
If you live in a country with a lot of laws restricting human rights (Iran, Turkey, China, etc.), we recommend to make at least two deposit-withdrawals via bitcoin services in a different jurisdictions. Remember that those services might relase any user data to law enforcement if ordered to do so. Some examples of services we can think of are a Bitcoin exchange in Philippines, Mexico, Brasil, South Africa, combined with Localbitcoins, a gambling website, etc. Just make sure the services are legal in your jurisdiction.
Best practices
In the end, we present to you list of best practices that will help you to keep your transactions private.
- Always assume that all transactions from a particular wallet are linkable (never buy anonymous stuff and personal stuff with bitcoins from the same wallet).
- Always use Tor Browser when you are buying something with bitcoins from the anonymous wallet (your real IP address will remain unknown to the merchant).
- Always connect to Electrum servers via Tor (your real IP address will remain unknown to the Electrum server admin).
- Use the Tor Browser with disabled JavaScript if the mixing service supports it (LE used some JavaScript exploits in the past to deanonymize Tor users).
- Use at least two mixing services in a row to anynimize the bitcoins. Like this: LocalBitcoins.com → mixing service A → mixing service B → anoynymous-wallet (your transactions will remain private also in the case when one of the mixing services is compromised).
- If the mixing service requires user registration then use a different account for every mixing operation (this will prevent the mixing service to enumerate all your wallets).
- Use only well established mixing services and look for reviews on the internet before using them.
- Use only encrypted communication channels to contact the mixing service (unencrypted email can be easily intercepted). Bitmessage for example, is encrypted, anonymous, decentralised and uncensorable.
References
- Fergal Reid; Martin Harrigan (2011). "An Analysis of Anonymity in the Bitcoin System"
- Gregory Maxwell (2013-08-22). "CoinJoin: Bitcoin privacy for the real world". bitcointalk.org.
- Chris Belcher (2015-01-09). "Joinmarket - Coinjoin that people will actually use". bitcointalk.org.
- Gregory Maxwell (2015-06-09). "Confidential Transactions, Content privacy for Bitcoin transactions". bitcointalk.org.
- David Chaum, Untraceable electronic mail, return addresses, and digital pseudonyms, Comm. ACM, 24, 2 (Feb. 1981); 84-90
- Thin Client Security - Bitcoin Wiki